-
Breaches
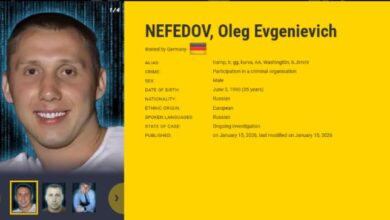
Black Basta Ransomware Leader Added to EU Most Wanted and INTERPOL Red Notice
Ravie LakshmananJan 17, 2026Law Enforcement / Cybercrime Ukrainian and German law enforcement authorities have identified two Ukrainians suspected of working…
-
Breaches
GootLoader Malware Uses 500–1,000 Concatenated ZIP Archives to Evade Detection
Jan 16, 2026Ravie LakshmananMalvertising / Threat Intelligence The JavaScript (aka JScript) malware loader called GootLoader has been observed using a…
-
Breaches

ThreatsDay Bulletin: AI Voice Cloning Exploit, Wi-Fi Kill Switch, PLC Vulns, and 14 More Stories
Jan 15, 2026Ravie LakshmananCybersecurity / Hacking News The internet never stays quiet. Every week, new hacks, scams, and security problems…
-
Breaches

Cybersecurity Predictions 2026: The Hype We Can Ignore (And the Risks We Can’t)
Jan 09, 2026The Hacker NewsArtificial Intelligence / Enterprise Security As organizations plan for 2026, cybersecurity predictions are everywhere. Yet many…
-
Breaches

China-Linked Hackers Exploit VMware ESXi Zero-Days to Escape Virtual Machines
Jan 09, 2026Ravie LakshmananVirtualization / Vulnerability Chinese-speaking threat actors are suspected to have leveraged a compromised SonicWall VPN appliance as…
-
Breaches

ThreatsDay Bulletin: RustFS Flaw, Iranian Ops, WebUI RCE, Cloud Leaks, and 12 More Stories
Jan 08, 2026Ravie LakshmananCybersecurity / Hacking News The internet never stays quiet. Every week, new hacks, scams, and security problems…
-
Breaches

ThreatsDay Bulletin: Stealth Loaders, AI Chatbot Flaws AI Exploits, Docker Hack, and 15 More Stories
Dec 25, 2025Ravie LakshmananCybersecurity / Hacking News It’s getting harder to tell where normal tech ends and malicious intent begins.…
-
Breaches

Attacks are Evolving: 3 Ways to Protect Your Business in 2026
Dec 24, 2025The Hacker NewsPassword Management / Access Control Every year, cybercriminals find new ways to steal money and data…
-
Breaches

INTERPOL Arrests 574 in Africa; Ukrainian Ransomware Affiliate Pleads Guilty
A law enforcement operation coordinated by INTERPOL has led to the recovery of $3 million and the arrest of 574…
-
Breaches

Nigeria Arrests RaccoonO365 Phishing Developer Linked to Microsoft 365 Attacks
Dec 19, 2025Ravie LakshmananCybercrime / Law Enforcement Authorities in Nigeria have announced the arrest of three “high-profile internet fraud suspects”…
